Using Office 365 email service with GCC High accounts
As you probably know, Microsoft has disabled Basic Authentication for SMTP, Office365 API, IMAP and other protocols, moving towards "oAuth 2.0". This is not a problem, Jitbit Helpdesk supports O365 oAuth flow out of the box, our app is alreaddy listed for the "Global" Microsoft cloud. However, if you're using "GCC High" aka "Microsoft Government Cloud", then some additional steps are required. You will have to create an "app registration" in GCC Azure portal yourself, and then provide its details back to Jitbit Helpdesk.
Creating an app registration
- Open https://portal.azure.com/
- Open Azure Active Directory
- Click on App registrations
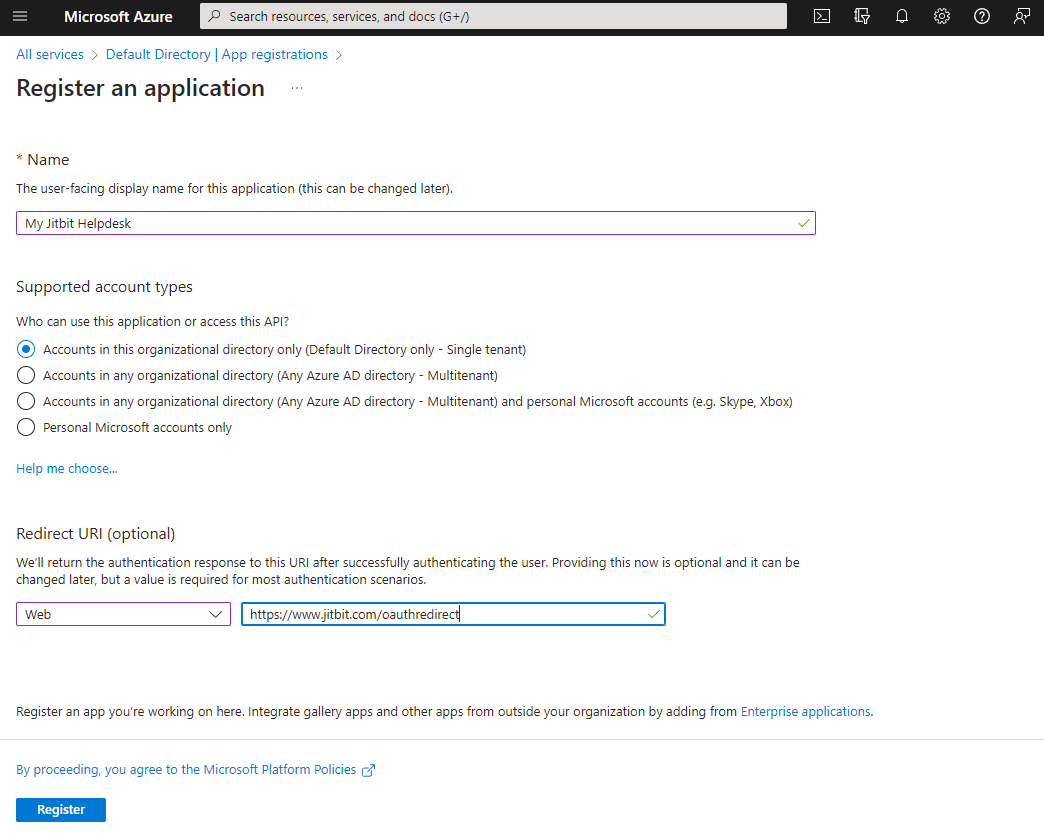
- Click on New registration
- Pick a friendly name
- Set "platform to "web" and "Redirect URI" to
https://www.jitbit.com/oauthredirect
Setting app permissions
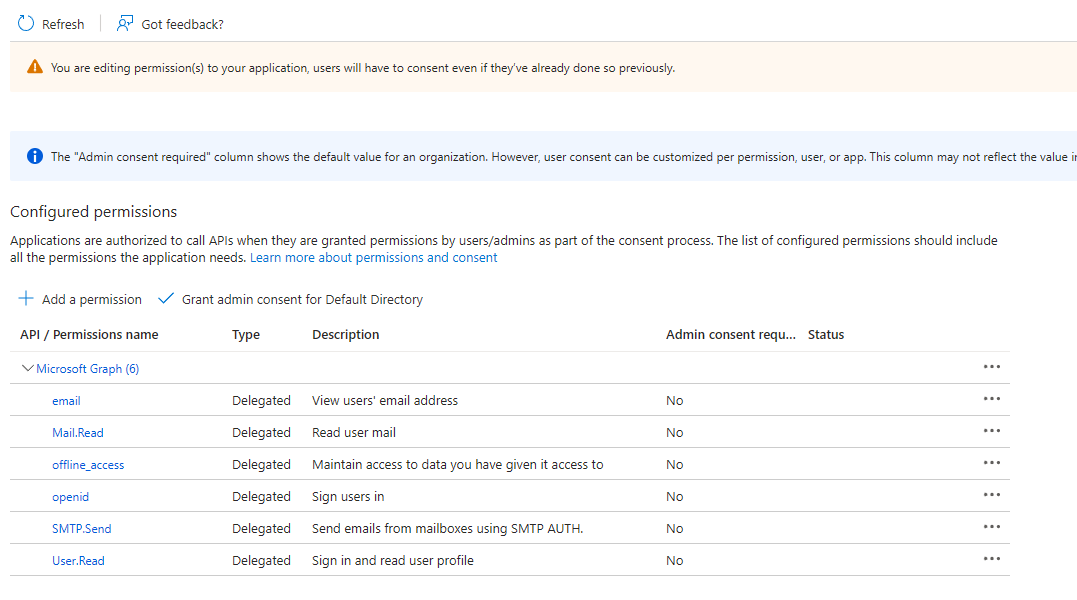
- Select API permissions
- Select Add a permission
- Select Microsoft Graph
- Select Delegated permissions
- Use the search box to add the following permissions: email, offline_access, openid, Mail.Read, SMTP.Send
- After saving permissions click on "Grant admin consent"
- Select Certificates & secrets
- Click on New client secret
- Copy the Value generated and save it somewhere, this "Value" will be needed in Jitbit Helpdesk.
- Go to Overview and copy the Application ID, it will also be needed for Jitbit Helpdesk
Jitbit side
Now in Jitbit Helpdesk you can use GCC High for inbound and outbound email. Go to "Admin - Email - Outgoing email settings", where you set the SMTP settings. Select "Office 365" and check the "GCC" checkbox. After that enter the "Client-ID" and "Client-Secret" form the previous steps.
For inbound email go to "Admin - Email - Edit incoming mailboxes" to add an inbound email server. Select "Office 365 GCC" as the server type. The app will again prompt you for GCC app's "Client-ID" and "Secret" (they will be prefilled if you already set up the SMTP connector).
After setting this up, Jitbit will use GCC endpoints for oAuth flow
What about SAML SSO using GCC
No special adjustments needed for SAML via GCC, since when setting up SAML you have the option to specify IdP URLs directly, so it should work right out of the box.